|
|||||||||||||||||||||||||||||
|
|
|||||||||||||||||||||||||||||
|
Regular Papers Vol. 5, No. 10, pp. 36–45, Oct. 2007. https://doi.org/10.53829/ntr200710rp1 Interference Exploitation for Cognitive RadiosAbstractCognitive radios (CRs) operating in a frequency band owned by a legacy wireless communication system (often called the primary system) can be made more efficient if interference from the primary system is exploited instead of being regarded as a major disturbance that limits the opportunity to reuse the primary frequency band. However, since the primary system is a legacy system with known transmission parameters, the interference from the primary system should not always be treated as Gaussian-like noise. For a time-division-duplexing-based primary system, we show two examples of interference exploitation: (1) exploitation in the medium access control (MAC) layer to achieve distributed medium access for collocated CR networks (exploitation in the time domain) and (2) exploitation in the physical (PHY) layer where the interference from/to the primary system is cancelled/mitigated by using an adaptive array antenna (exploitation in the spatial domain). We show that such exploitation of interference can help cognitive radios efficiently reuse the primary spectrum in space and time.
1. IntroductionCognitive radio (CR)*1 has been proposed as a means to achieve efficient use of the radio spectrum [1], [2] and thus break the myth of spectrum scarcity. The basic concept is that a CR network is allowed to access the frequency spectrum assigned to a legacy system (called the primary system*2) as long as the interference conditions for the CR and the primary receivers are below an acceptable level. Such a secondary use of the spectrum is expected to provide wireless networks suffering from spectral congestion (e.g., wireless networks currently operating in the unlicensed spectrum such as wireless local area networks (WLANs)) with more opportunity to access the radio spectrum. If the primary system underutilizes the assigned spectrum segment, then the reuse of that segment can drastically improve the overall efficiency of spectrum utilization. In order for CR networks to satisfy the given interference condition, a CR transmitter should operate discreetly i.e., it should not cause harmful interference to the primary system. Furthermore, to satisfy the required quality of service (QoS) (such as throughput and delay), a CR network should operate efficiently even under interference from the primary system. So far, it has been considered that the key issue for achieving efficient operation is to avoid the interference from the primary system, which is regarded as a big disturbance for CR networks. However, considering that the primary system is a legacy system, which was deployed before the CR networks, it is reasonable to assume that the CR networks have certain knowledge about the transmission parameters of the legacy primary system. For example, the CR networks can know the traffic pattern, frame format, carrier configuration over frequency (i.e., the position of data and pilot carriers), modulation/coding parameters, etc. of the primary system. Furthermore, if the CR nodes are equipped with the full configuration of the radio interface of the primary system or with software defined radio (SDR) components [3], then they can also decode the primary signal. This is especially true when the interfering primary signal is sufficiently strong. In such a scenario, the interference from the primary system is not always Gaussian-like noise. Instead, it may carry decodable information that can be shared by the CR nodes and networks. This is particularly important when the primary system has a large service area that encompasses many CR networks. A key question here is what kind of information is available to the CR nodes and how such information can be exploited to enhance the overall performance of CR networks. In this paper, we advocate a new approach to achieving efficient operation of CR networks by exploiting the interference from the primary system instead of regarding it solely as a disturbance. We show two examples of such interference exploitation: (1) exploitation in the medium access control (MAC) layer to achieve distributed medium access for collocated CR networks (exploitation in the time domain) and (2) exploitation in the physical (PHY) layer where the interference from/to the primary system is cancelled/mitigated by using an adaptive array antenna to achieve efficient and discreet operation of CR networks (exploitation in the spatial domain). We also discuss future research topics that will be opened up by our approach of regarding primary interference as useful information. The rest of this paper is organized as follows. Section 2 presents our target scenario and model for coexistence between the primary*2 and secondary systems*3. Section 3 presents a medium access protocol that exploits the primary signal to coordinate the transmissions of distributed and independent CR networks. Section 4 presents a novel interference cancellation/mitigation technique that uses an adaptive array antenna, which exploits knowledge about the primary system as well as the signal of the primary system. Section 5 concludes with a summary of the main points and a discussion of future research issues.
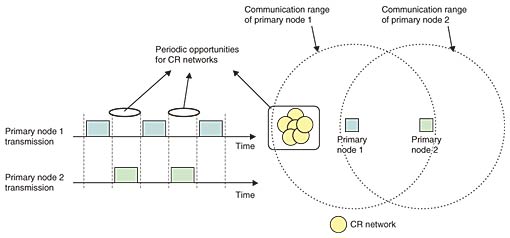
2. Interference exploitation: target scenarioWe consider CR networks that operate in a frequency band allocated to a primary system. We focus on the scenario where the CR networks coexist with the primary system, which means that the CR networks are within the interfering or communication range of the primary system. If the CR networks are not in such a coexisting condition, they do not suffer from primary interference and can operate as if the frequency band is allocated solely to the CRs. On the other hand, when the CR networks coexist with the primary system, they can find opportunities to successfully transmit and receive signals if the primary signal is inactive for some period or if the resulting interference is below an acceptable level. Here, we explore such a reusable area inside the primary service area, which can significantly increase the spectrum available to CR networks. Such an increase is more significant when the primary system has a wide communication range while the CR networks have small, short-range communication areas [4]. Therefore, in this section, we focus on the coexistence of a long-range primary system and short-range CR networks. One example for a long-range primary system is a fixed wireless relay/access such as fixed Wi-MAX, while some examples of short-range networks are WLANs and sensor networks. In the above coexistence scenario, one important requirement for the CR transmitter is not to cause unacceptable interference to the primary receivers. There are two different ways to handle such interference. One way is to regulate the transmission of each CR transmitter (e.g., possible transmission area and maximum transmission power) so that the primary receiver does not experience an unacceptable interference level. The other way is for the primary system to allow CR nodes to make transmissions in any area, but to require each CR transmitter to make the best effort to minimize the interference to primary receivers. We discuss the regulated case in Section 3 and the best-effort case in Section 4. We consider that the primary system is a legacy system that was deployed in a certain area before the CR networks. We assume that the CR networks have certain knowledge about the legacy primary system and we investigate how different amounts of knowledge and information can be exploited to achieve different benefits for CR networks. 3. Exploitation in time domain: distributed medium accessIn this section, we consider interference exploitation for the MAC-layer operation of CR networks. In this case, there are many collocated CR networks within interfering range of each other, and they attempt to utilize a portion of the spectrum owned by the primary system. Such a scenario can occur if we consider a hotspot of WLANs that are based on cognitive radio technology. We assume that these networks are supposed to operate in a completely distributed and independent manner, meaning that they cannot communicate with each other to coordinate their transmissions. We consider that CR networks coexist with a primary system that has a periodic traffic pattern. Such periodic traffic could be generated by, for example, a beacon system that broadcasts information over its service area with a certain period of time. Another good example is the case when the primary system uses time division duplexing (TDD), which results in periodic interference to CR networks. This situation is depicted in Fig. 1. Here, the primary system has a point-to-point TDD link between nodes 1 and 2. In this case, the CR nodes located inside the communication range of primary node 1 experience strong interference when primary node 1 is transmitting. However, if these CR nodes are outside the range of primary node 2, they can experience weak interference when primary node 2 is transmitting, which can generate periodic opportunities for CR networks. Note that, in this section, we assume that the transmission power of CR nodes is regulated so that it does not cause harmful interference to the primary receiver. Thus, what a CR node has to do to achieve successful packet transmission is to find a period when it will not have simultaneous transmission with the primary system or other CR nodes.
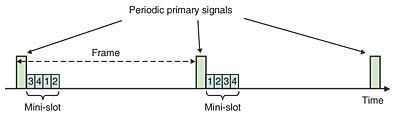
The difficulty in achieving an efficient medium access in the above distributed condition comes from the fact that there is no central entity to coordinate the transmissions and that the independent networks cannot communicate with each other to share common information. However, since we treat a legacy primary system whose signal is transmitted widely, each CR network can obtain the following common information from the primary signal. (1) Common frameEach CR node uses the primary signals as a common clock. Thus, each node detects the primary signals and sets the start of a primary signal to the beginning of a frame, which is shared by all the CR nodes. Thanks to this operation, CR nodes can have a global clock, i.e., a framed channel in a distributed manner. (2) Common random numberWe assume that CR nodes can decode the primary signal and that they decode each periodic primary signal. We define N bits of information in a certain field of the primary packet (e.g., the first N bits of a packet) as a bit sequence that is observed by all the CR nodes. We define in advance the mapping between each possible bit sequence and an integer between 1 and M. We call the resulting random integer the common number (CN). The mapping is made so that CN takes an integer value between 1 and M as uniformly as possible. This number can change every frame because the information included in the primary signal can be differ frame by frame, but all CR nodes can share this number for each frame, which can basically create a common numbering scheme for each frame. Thus, CR nodes exploit the primary signal as a beacon to create a logical time frame to be used by independent CR networks. Here, we propose a medium access protocol called interference-aided medium access (IAMA) that can achieve distributed time division multiple access (TDMA) with the above information obtained from the primary signal. Note that such a TDMA operation can also be achieved with reservation-based random access such as packet reservation multiple access (PRMA) and reservation ALOHA [5]; however, these protocols require a central coordinator or pre-configured frame structure. Below, we briefly describe the basic operation of IAMA. For details of the procedure, readers are referred to [6].
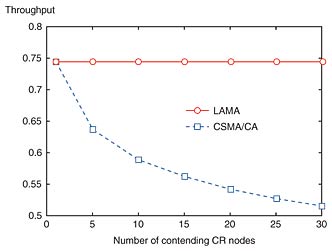
The above operation achieves prioritized transmission in each frame. Thus, the ordering of the mini-slots determines the priority to be applied in each frame. For example, in the first frame in Fig. 2, the CR nodes with Access Sets that include 3 have the highest priority for transmitting packets. The CR nodes can transmit a packet in each frame if there are no contending CR nodes with higher priority. The advantage of this medium access is that, once CR nodes find the Access Set that enables successful packet transmission, they can achieve collision-free transmissions unless new CR nodes (networks) arrive in the contending area. Simulation results for the throughput of our scheme IAMA and the basic CSMA/CA scheme are shown in Fig. 3. Note that CSMA/CA is a representative medium access protocol that operates in a distributed manner, that is, without any central coordinator or information exchange among contending nodes. Since no other specific MAC schemes for CR systems have been proposed yet, we compared IAMA with the basic CSMA/CA scheme. Here, with the CSMA/CA mode, the CR nodes contend for the medium only while the primary signal is absent. The throughput is defined as the fraction of time used by the successful (data) packet transmissions. We assume that the CR nodes are fully loaded, so each node always has packets to transmit. Other details of the simulation scenario and parameters can be found in [6]. From the figure, we can see that the throughput performance of the CSMA/CA scheme is much lower than that of IAMA. This is because CSMA/CA necessarily involves contention to the medium for each packet transmission and enters a back-off process to resolve the contention. On the other hand, IAMA can achieve collision-free transmission most of the time and can achieve high throughput performance irrespective of the number of contending CR nodes. This is similar to the effect of PRMA or reservation ALOHA under highly congested conditions, though IAMA achieves such a behavior not by explicit central coordination or by using a pre-configured frame but by coordination achieved by utilizing the primary signal.
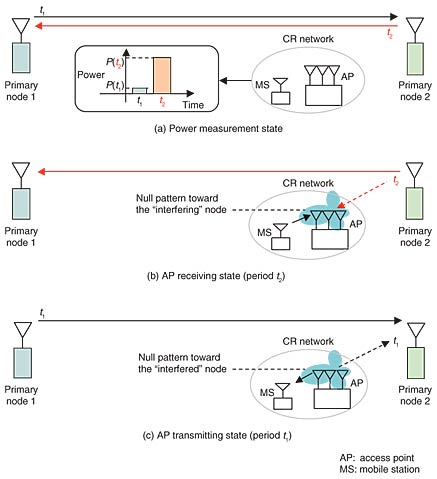
There can be further application of the above common information among different CR networks. For example, in [7], the performance of Bluetooth networks, which utilize frequency hopping, is analyzed when multiple small networks (termed piconets) coexist and interfere with each other. This section shows that inter-piconet interference can severely degrade the throughput performance; however, if multiple piconets are somehow synchronized, the degradation can be smaller. The authors of [7] did not provide a way to synchronize those multiple piconets because it is generally difficult to synchronize such networks due to the lack of a synchronization mechanism, geographical location (different networks can interfere with each other, but are not necessarily within communication range of each other), etc. However, if such different frequency-hopping-based networks coexist in the frequency band assigned to the primary system with periodic traffic, they can be synchronized to each other by using the interference, as described in this section, and the throughput degradation can be greatly alleviated. Such “global timing synchronization” is a valuable assumption in many distributed algorithms for medium access [8], which can be obtained with our interference exploitation approach. 4. Exploitation in spatial domain: interference cancellation/mitigation with adaptive array antennaIn this section, we introduce a PHY-layer approach for exploiting interference. We introduce a new technique in which CR nodes exploit knowledge about the primary system and the signal of the primary system to cancel/mitigate the interference from/to the primary system in the spatial domain by using an adaptive array antenna. This scheme can achieve efficient operation of the CR receiver, thus canceling the interference from the primary system, as well as discreet operation, thus mitigating the interference from the CR transmitter to the primary receiver. This allows CR nodes to reuse the primary frequency band even if they are located close to the primary node. This exploitation technique can be applied to a primary system that utilizes TDD or frequency division duplexing (FDD). More precisely, the key point of our scheme is for CR nodes to observe a pair of TDD periods, (t1, t2), which are the transmitting or receiving timings for a primary node, or a pair of FDD frequency bands, (f1, f2), which are the transmitting or receiving bands for a primary node. We assume that the CR nodes have knowledge about these transmission parameters of the primary system and that they know the exact timing for the pair of periods to appear (TDD case) or the exact frequency bands (FDD case). In this section, we give details of our scheme for only the TDD case. The operation of the interference cancellation/mitigation scheme is shown in Fig. 4. We assume that there are two primary nodes operating in TDD mode with a repeated pair of periods (t1, t2). Primary node 1 (node 2) transmits (receives) the signal during period t1 while primary node 2 (node 1) transmits (receives) the signal during period t2. The first step of the scheme is for CR nodes to detect and measure the power levels P(t1) and P(t2) in t1 and t2 (step (a) in Fig. 4). Then, the power levels P(t1) and P(t2) are compared; according to the results of the comparison, CR nodes make the following decisions:
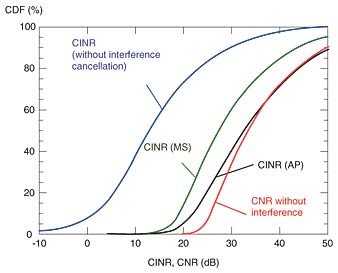
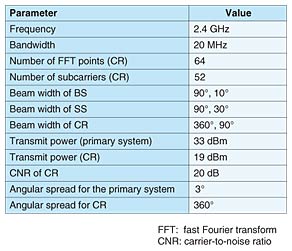
Figure 4 shows an example where a CR network is closer to primary node 2, and it observes a higher interference level during period t2. While the interference cancellation technique is required to achieve successful transmission during t2 due to the high interference level, CR nodes have the potential to achieve successful transmission even without the cancellation technique during t1 thanks to the lower interference level. However, the large power level in t2 and small power level in t1 mean that primary node 2 is likely to be in the vicinity of the CR nodes. This can be judged because the received signal power basically depends on the propagation path loss, which is dominated by the distance between the transmitting and receiving entities. In such a case, the transmission of CR nodes during t1 can cause interference to primary node 2. Since the primary systems are not necessarily designed to avoid such interference, CR nodes should make the best effort to minimize such interference in order to achieve discreet operation. To enable CR nodes to overcome such interference from/to the primary system, our scheme operates as follows. First, the CR nodes cancel the interfering signals by making a null pattern in the direction of the signals with the higher power level (i.e., the signal arriving during t2), as shown in Fig. 4(b). Here, as an example, we use an adaptive array antenna at the access point (AP) of the CR network. As an adaptive algorithm for interference cancellation, the minimum power method or eigenvalue decomposition can be utilized [9]. With this operation, we can let a mobile station (MS) transmit signals during t2, and the AP can receive the signal while reducing the amount of interference. Note that such a transmission by an MS is unlikely to interfere with the reception at primary node 1 because the distance between them is large. Next, during period t1, the AP transmits signals to the MS by using the weights that were calculated to create a null pattern during t2, as shown in Fig. 4(c). Since the same frequency band is used for transmission and reception in TDD mode, the weights calculated during t2 to create a receiving null pattern can be reused to create a transmitting null pattern that is appropriately directed toward the primary receiver. Such a transmission by the AP can mitigate the interference to primary node 2. Thus, the interference observed during t2 is exploited to identify the direction of the primary receiver, which could suffer interference from the transmission of CR nodes. By using this scheme, we can achieve close coexistence between the CR nodes and the primary system because the CR nodes can cancel/mitigate the interference from/to the primary system. Knowledge about the primary system and the signals of the primary system are exploited to enable CR nodes to find appropriate timings and null patterns for their transmission and reception. This can open up more opportunities for the CR nodes to reuse the primary frequency band. The cumulative distribution function (CDF) of the carrier-to-interference-plus-noise ratio (CINR) with and without our scheme is shown in Fig. 5. The simulation parameters are shown in Table 1. The propagation path loss used here, which was taken from [10], enables us to evaluate the performance for various antenna heights. In other words, heterogeneous path loss conditions can be taken into account for different links such as the transmission between the primary transmitter and receiver and the interference from the primary system to the CR nodes, as well as the interference from the CR nodes to the primary receiver. We considered two entities in the primary system—a base station (BS) and a subscriber station (SS)—and set the heights of their antennas to 30 and 2 m, respectively. In order to examine the characteristics of our scheme under less favorable conditions for CRs, we assumed the antenna height of a CR node to be 20 m, where the path loss from BS to CR nodes is much smaller than the path loss between BS and SS. The number of antennas at the AP was set to 2, and the location of CR nodes was randomly changed inside the service area of the primary system.
From Fig. 5, we can see that the CINR without our interference cancellation/mitigation scheme was strongly degraded (thus there was a high probability of having a lower CINR) due to the strong interference from the primary system. On the other hand, with interference cancellation/mitigation, the CINR value was significantly improved, and the performance at the AP was close to the case without the primary interference. Moreover, the CINR of the MS in the CR network was much higher than the condition with the greatest interference even without the interference cancellation at the receiver because the transmission was performed during the period with less interference (i.e., t1 in the example in Fig. 4). We have also confirmed that the degradation of CINR at the primary receiver is very small thanks to the transmission by the AP with the appropriate null pattern toward the primary receiver. 5. Concluding remarksIn this paper, we advocated exploiting interference from the primary system to enhance the communication performance of CR networks. Instead of regarding the interference from the primary system as just a disturbance, we can use the knowledge about transmission parameters and also use the actual interference signal of the primary system to increase the opportunities for CR networks to reuse the primary frequency band. For a TDD-based primary system, we showed examples of such exploitation, namely exploitation in the MAC layer to achieve distributed medium access among cognitive radios (exploitation in the time domain) and exploitation in the PHY layer to achieve interference cancellation/mitigation from/to the primary systems with the use of an adaptive array antenna (exploitation in the spatial domain). Although we discussed such exploitation mechanisms for a TDD-based primary system with periodic transmission/reception patterns, such periodicity is not a necessary condition for these mechanisms. Instead, these mechanisms can be applied as long as CR nodes can identify the transmission/reception timing of primary systems, which could be obtained by, for example, decoding the control information transmitted by the primary nodes. Our approach of exploiting the primary interference could open up several future research topics. First, the interference from the primary system is far less random than Gaussian noise, and even more important, a CR can decode the signals from the primary system. Thus, the receiver of the cognitive radio observes a multiple access channel of two users, one being the desired transmitter and the other being the undesired primary transmitter. In principle, the receiver can try to decode both signals jointly e.g., through successive interference cancellation. Such an operating mode will give the CR more spatial capacity because it will be able to operate in regions of high interference by decoding and subtracting that interference. Clearly, it is desirable to not only quantify the gain provided by such an operating mode, but also devise practical methods of implementing such interference decoding/subtraction. Second, combined exploitation strategies for PHY/MAC layers should be investigated, e.g., the two mechanisms described in this paper should be integrated so that CR nodes can efficiently share the spatial/temporal opportunities created by the interference cancellation/mitigation technique. Finally, further investigation of possible transmission parameters that CR nodes can exploit is required. In this paper, the key information and parameters for the interference exploitation were the duplexing mode (TDD) of the primary system. However, CR nodes could also know other parameters of the primary system, such as modulation/coding and frequency-carrier configuration. Exploitation of such information could further enhance the efficiency of CR nodes in reusing the primary spectrum, which could result in higher utilization efficiency of our precious frequency resources. AcknowledgmentThis work is in part supported by the Danish Research Council for Technology and Production Sciences (Project No. 274-05-0490). References
|
|||||||||||||||||||||||||||||