|
|
|
|
|
|
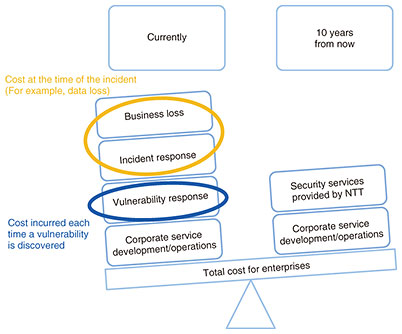
Feature Articles: Encryption and Security Technologies for Creating a Safe and Secure Society Vol. 19, No. 6, pp. 81–87, June 2021. https://doi.org/10.53829/ntr202106fa13 Establishment and Development of Cybersecurity Technologies to Solve Problem of Increasing Operation Costs and to Minimize DamageAbstractWhile responding to new cybersecurity threats such as cyber attacks, we will radically improve the efficiency of security operations by developing technologies for autonomous and automated security measures. Such technologies will enable operators to concentrate on countermeasures against advanced threats that cannot be handled mechanically and enhance overall security-response capabilities. Keywords: cybersecurity, security operation, security measures 1. BackgroundCyber attacks are increasing yearly and becoming more complicated and sophisticated. In particular, there has been a significant increase in cyber attacks that directly target humans, which has dramatically increased the cost of cybersecurity measures for enterprises. When users have diverse requirements and enterprises need to cope with long tail customers, a variety of applications should be provided through a combination of servers and software on ultrahigh-speed optical communication networks connecting various communication equipment, terminals, and devices. In such a situation, the efficiency of security measures to handle each cyber attack is too low, which can be a factor hindering the digital transformation and business-value creation of enterprises. 2. Goal of our research and developmentWe are conducting research and development (R&D) on technologies for automatically and proactively implementing security measures against cyber attacks and various vulnerabilities that are targets of them. Through such technologies, we will provide an information and communication technology (ICT) environment capable of preventing damage caused by cyber attacks and resolving the shortage of human resources in security operations that restrict enterprise management, enabling users to use services with peace of mind. This environment eliminates the need for enterprises to respond to security vulnerabilities each time (whack-a-mole game), after an incident (cat-and-mouse game), or respond to business loss due to damage (Fig. 1).
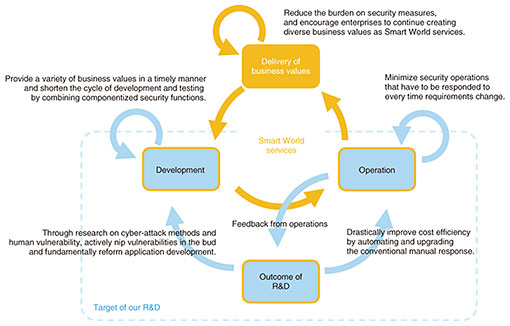
By reducing the total cost of security operations, we will enable enterprises to focus on development and operations and support them in creating business values in short cycles in a Smart World of smart factories, buildings, mobility, etc. (Fig. 2).
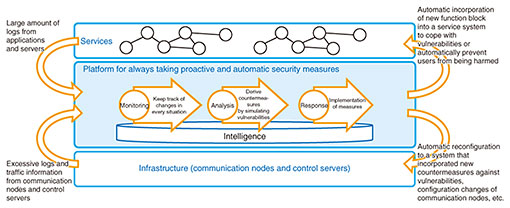
3. Platform as a result of our R&DIn security operations, many security measures, such as monitoring, analysis, and response, are implemented manually, so the ability to carry them out depends heavily on human skills. By implmenting a platform with our technologies, we will constantly monitor the status of devices and applications that make up infrastructure and services and automatically execute security measures on systems in advance as soon as a vulnerable situation is found. The platform provides an environment to conduct stable, effective, and efficient security measures (Fig. 3).
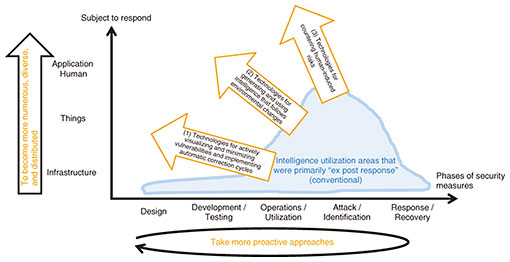
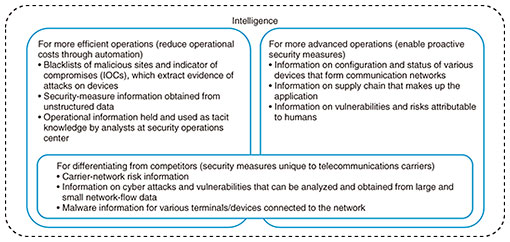
4. Challenges in implementing the platformTo automatically and proactively implement security measures, we will conduct R&D on the following three technologies (Fig. 4) and create intelligence, as shown in Fig. 5.
(1) Technologies for actively visualizing and minimizing vulnerabilities, and implementing automatic correction cycles To provide robust security, we will conduct R&D on visualizing and minimizing vulnerabilities, and also on implementing automatic correction cycles to enable shift-left security measures that can nip vulnerabilities in the bud and drastically improve efficiency of security operations. (2) Technologies for generating and using intelligence that follows environmental changes Security measures are continuously and autonomously implemented in a wide variety of ICT environments through technologies for automatically generating intelligence unique to telecommunication carriers and automatically using intelligence that does not require awareness. (3) Technologies for countering human-induced risks We will conduct R&D on security technologies that can respond to risks arising from humans and drastically reduce risks related to human errors, fraudulent attacks targeting humans, internal fraud by employees, etc., which can lead to security damage. In the following section, we introduce our major R&D efforts. 5. Current activities(1) Configuration and status analysis technology (Fig. 6)
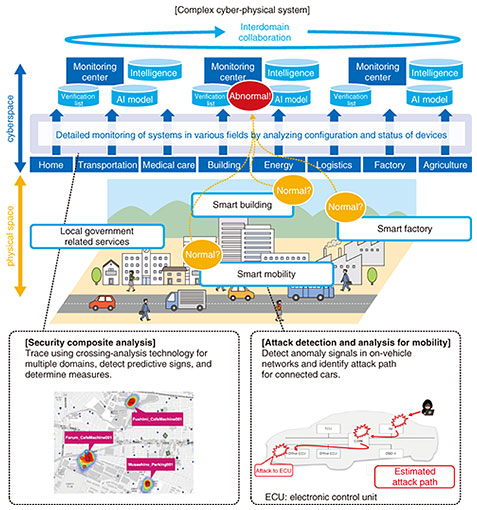
We are currently conducting R&D on software agents and communication-analysis engines that analyze the configuration and status of Internet of Things devices for people and things as a security technology to protect complex cyber-physical systems composed of various elements such as smart cities. We will conduct R&D on crossing-analysis technology for multiple domains to detect signs of security anomalies and estimate probable causes and measures, which have been difficult in the past, by analyzing the correlation between elements across systems and services in addition to configuration and status. (2) Initial-forensic-investigation technology (Fig. 7)
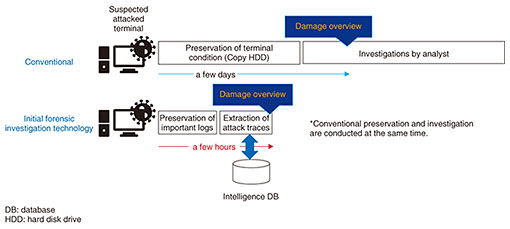
In cyber forensic investigation, a terminal that is suspected of being attacked is preserved, and a security analyst extracts evidence of an attack. While detailed analysis is possible from investigation by humans, it depends on the analyst’s experience and can take several days. In the initial investigation phase, therefore, its accuracy and speed remain issues for early clarification of the entire damage. Therefore, we are developing a technology for preserving only important logs and automatically extracting traces of attacks. The goal with this technology is to create an intelligence database of attack procedures that are often used by attackers and processing them automatically. Initial investigations can be conducted in a few hours, regardless of the skill levels of analysts. (3) Technology for detecting web-based social-engineering attacks that exploit human psychological vulnerabilities (Fig. 8)
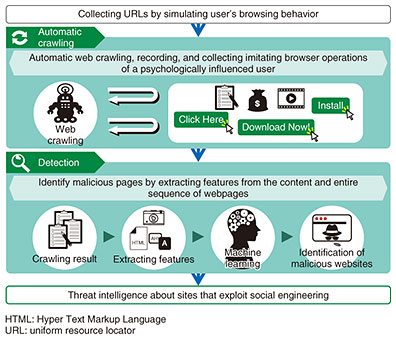
Attackers use opportunities such as international sporting events and the spread of COVID-19 infection to attract people’s interests and carry out cyber attacks that deceive users. Attackers can trick users into visiting a malicious site with interesting content or fake warning messages, causing malware infections and theft of money and personal information. We are conducting R&D on technology that can emulate the browser operations of deceived people, automatically crawl and collect webpages, and detect malicious sites with high accuracy and speed based on the image, language, and feature amount of the arrival path with the aim of reducing fraud damage targeting such people. 6. For the futureCybersecurity risks can now threaten countries and are one of the most serious social problems. As the situation continues to be dominated by attackers, we will continue to contribute to the betterment of society by creating new security technologies that can overcome the current severe cybersecurity situation. |