|
|||||||||
|
|
|||||||||
|
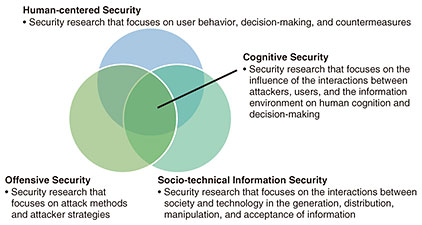
Front-line Researchers Vol. 23, No. 10, pp. 7–13, Oct. 2025. https://doi.org/10.53829/ntr202510fr1  Working towards Establishing Cognitive Security to Counter Threats Related to Cognition from Human-centered, Offensive, and Socio-technical Perspectives on SecurityAbstractSeveral incidents caused by cyber-attacks have been reported globally. They include information leaks due to ransomware, transportation disruptions due to DDoS (distributed denial of service) attacks, fraudulent contracts and resales due to malicious programs that abuse generative AI (artificial intelligence), data tampering due to SQL (Structured Query Language)-injection attacks and unauthorized access, and fraud using deep fakes. Avoiding such incidents necessitates a multifaceted response that includes measures to stop cyber-attacks, technology for minimizing the impact and spread of cyber-attacks, and defenses that rely on human psychology and behavior. Mitsuaki Akiyama, a senior distinguished researcher at NTT Social Informatics Laboratories, is researching security from the three perspectives of “human-centered security,” “offensive security,” and “socio-technical information security.” We spoke with him about these three themes related to cybersecurity and new research in their common areas as well as his philosophy of questioning and updating one’s experience and knowledge instead of solely relying on them and striving for mutual understanding and shared motivation to promote interdisciplinary research. Keywords: geographic skew, secure development guideline, browser permission mechanism, cognitive security Focusing on three themes: “human-centered security,” “offensive security,” and “socio-technical information security” and cross-disciplinary research among them—Could you tell us about the research you are currently working on? My research focuses on three themes: (i) “human-centered security,” security research that focuses on user behavior, decision-making, and countermeasures; (ii) “offensive security,” security research that focuses on attack methods and attacker strategies; and (iii) “socio-technical information security,” security research that focuses on the interactions between society and technology in the generation, distribution, manipulation, and acceptance of information (Fig. 1).
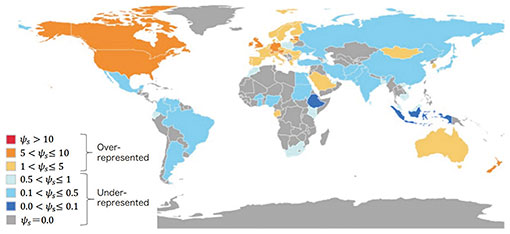
In my previous interview (August 2022 issue), I introduced (i) detecting threats to web re-hosting services, (ii) secure software development focusing on developers and development projects, (iii) countermeasures against phishing emails for non-native English speakers, (iv) correct methodology for user studies, and (v) an analysis of the mechanisms by which disinformation and misinformation spread on social media. Although I have been working on these themes individually, in addition to individual research focused on human-centered security and socio-technical information security, I am currently working on two cross-disciplinary research topics, “offensive security × human-centered security” and “socio-technical information security × human-centered security.” Research on human-centered security involves two tasks: (1) Quantitative analysis of geographic skew in user-survey research in the fields of security and privacy In the field of research on human-centered security, psychological and behavioral characteristics are revealed through user surveys; however, previous studies have focused on Western-based subjects and have been geographically skewed. Consequently, in-depth analysis as well as insights into aspects such as the universality of the survey results to all of humanity, existence of geographical differences in the results, and other points of difference have been insufficient, and an overall picture has not been revealed. With these insufficiencies in mind, using a systematic literature review that systematically and comprehensively searches, evaluates, and consolidates papers in a research field, my research partners and I identified 715 research papers in the field of human-centered security and privacy and analyzed them using a method that ensured inter-rater reliability by multiple analysts in terms of participants’ country of residence, attributes, recruitment method, research method, and research topic. This literature review revealed that there is a large skew in the number of user-survey samples targeting non-Western populations (a tendency toward Westerners) in the fields of security and privacy. On the contrary, a similar literature review in the field of human-computer interaction (HCI) found that the skew in the number of samples from non-Western countries tends to be mitigated and revealed that the skew tends to be more pronounced in the fields of security and privacy. A study on the degree of investigation in each country based on the proportion of the world population revealed that Western countries, such as the United States, the UK, and Germany, are over-investigated relative to their proportion of the world population. In contrast, it was found that investigations are insufficient in relation to the proportion of the world population in Asia, including Japan, and most non-Western countries, such as in the Middle East, Africa, and South America (Fig. 2). These results raise the issue of correcting skew in investigation subjects in security and privacy and suggest future directions for research.
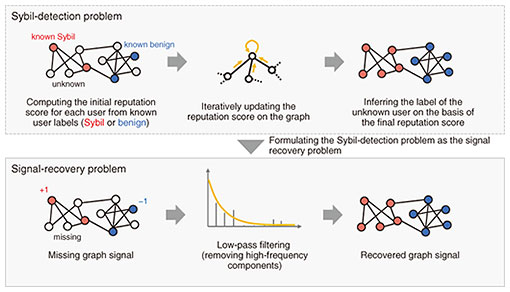
Focusing on a user-survey research method for eliminating the Western skew revealed in our literature review and understanding diverse populations, we proposed to overcome geographical and linguistic barriers by promoting replication studies on non-Westerners in two ways: (i) clarifying the generalizability of research results and differences between people on the basis of geography and culture and (ii) using local crowdsourcing services used in the countries where the target users reside and collaborating with researchers who are familiar with local languages, cultures, and environments to enhance researcher diversity. These studies were conducted in collaboration with the National Institute of Information and Communications Technology (NICT) and presented at USENIX Security 2024, one of the top international conferences on cybersecurity, held in Philadelphia, USA from August 14 to 16, 2024 [1]. (2) Research on the current state of use and operational issues regarding secure development guidelines for industrial development sites in Japan and the United States Developing secure software is essential for supporting the foundation of the information society, and secure development guidelines describe methods and guidelines for software design and implementation for that purpose. While most academic research focuses only on publicly available secure development guidelines, there has been little research on the actual usage of the guidelines and operational issues concerning industrial software-development sites. Our research revealed that in actual industrial development sites, each company’s in-house secure development guidelines are more widely used. It also revealed that the feasibility of the methods of effectively implementing secure development guidelines (e.g., verifying whether development complies with the guidelines) proposed depends on the nature of the developer’s organization. Our research also shows that it can be particularly difficult to implement the guidelines in small-scale development projects or contract development due to factors such as the discretion given to developers and cost constraints. All the research results that I mentioned above clearly show the gap between academia and industry regarding secure development guidelines and have contributed to clarifying the issues involved in promoting the development of secure software. It is hoped that promoting secure software development on the basis of these survey results will lead to the deployment of secure systems and services that users can use with peace of mind. These results were accepted and presented at the top international conference on HCI, the CHI Conference on Human Factors in Computing Systems (CHI 2023) held on April 23–28, 2023 [2]. Regarding socio-technical information security, we are researching technologies to counter attacks by fake accounts (Sybil: a group of malicious bots) that are used to spread spam uniform resource locators (URLs), fake news, and false information on social media. Attacks by bots through social media that sent spam URLs, fake news, and false information via Sybil had been easily detected from account-activity patterns, and countermeasures against such attacks could be implemented. However, bots that attempt to evade detection by interweaving harmless posts with harmful ones, imitating the characteristics and behavior of legitimate users or occasionally being controlled by humans to interact with other users, have appeared and are more difficult to detect. Since legitimate users rarely intentionally follow malicious bots, we used the following three network characteristics: (i) connections between bots and legitimate users are inevitably likely to be sparse; (ii) malicious bots can be detected by skillfully identifying structural gaps between bots and legitimate users in the network of accounts; and (iii) manipulating the following behavior of legitimate users is generally difficult for attackers, and if they try, evading detection is also difficult. We also reduced the Sybil-detection problem to a signal-restoration problem in graph signal processing. Through these actions, we established a methodology that enables theoretical comparison and analysis of various detection methods (Fig. 3).
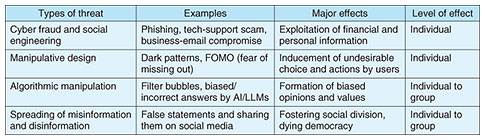
Using this methodology, we identified the requirements for a Sybil-attack-detection method to achieve high performance and proposed a detection method that meets these requirements. We confirmed through numerical experiments that regardless of the graph structure, the proposed method achieves stable and high performance in comparison to other methods. Our paper on the above research results was published in the January 2023 issue of the IEEE’s Transactions on Information Forensics and Security, a leading international journal in the security field [3]. —What efforts are you making in cross-disciplinary research? Regarding cross-disciplinary research between offensive security and human-centered security, we clarified the web-browser permission mechanism. A web browser’s permission mechanism controls the operations that web pages can execute on a computer or smartphone. For example, it enables the user to choose whether to allow access to a microphone or camera on a web page that uses audio or video. We focused on the fact that there are differences in implementation of this permission mechanism in a wide variety of web browsers and identified methods for efficiently evaluating these implementation differences and new security and privacy threats based on those implementation differences. Typically, multiple web browsers are not used in parallel, and differences in the implementation of the permission mechanisms of each web browsers go unnoticed. Differences in implementation can lead to incorrect implementations or bugs due to errors, which can pose threats to security and privacy. Considering such threats, we created an environment in which various web browsers running on devices can be run side by side and evaluated; it thus became possible to compare and evaluate web browsers running on various operating systems comprehensively. We therefore discovered numerous implementation errors and bugs in permission mechanisms as well as exposing new security and privacy threats, such as phishing and tracking, that exploit those errors. We also conducted a user survey and quantified the negative impact that the discovered threats have on the perceptions and behaviors of users. On the basis of these results, we proposed to web-standardization organizations that they share best practices and standardize web-browser permission mechanisms. A paper on this study was accepted for presentation at the Network and Distributed System Security Symposium (NDSS) 2023, one of the four major international conferences on cybersecurity, held from February 28 to March 2, 2023 [4]. As cross-disciplinary research between socio-technical information security and human-centered security, we aim to make users aware of the malice (spreading information through emotional manipulation) behind information. Misinformation and emotionally manipulative content, often posted by artificial intelligence (AI) and large language models (LLMs), are becoming increasingly commonplace. Meanwhile, social-media platforms are scaling back their fact-checking capabilities. And fact-checking faces limitations. This situation poses an increasing risk to public health and autonomous decision-making. One way to address these issues is to detect whether content contains expressions that manipulate emotions and present the detection results to users in a way that is expected to prevent them from carelessly believing the content or sharing it with others. We verified the effectiveness of this warning label for emotionally manipulative language. Specifically, we investigated the impact of the accuracy of information and presence or absence of warning labels on user reactions to health-related social media posts. The results of our investigation revealed that in regard to content that contains emotionally manipulative language, warning labels can sometimes have the effect of encouraging introspective behavior (such as refraining from careless sharing) regardless of whether the content is legitimate. In consideration of these results, we offered recommendations for platform strategies to mitigate the impact of misleading or manipulative content as well as guidelines for future research. In recognition of our papers being accepted at these top international conferences and academic societies, I was appointed to the program committees of NDSS in 2024 and USENIX Security in 2025. Very few program committee members are from Japan, and at that time, I was the first Japanese researcher to be appointed to the program committee in the 30-year history of NDSS. I was also awarded the NDSS 2025 Distinguished Reviewer in recognition of my outstanding contributions (high-quality peer review, leading discussions within the committee, and dedicated shepherding activities) among the world’s leading researchers. As I pursued these studies from different perspectives, I realized that the overlaps among them are particularly important. For example, when offensive security uncovers a new threat, it becomes necessary to investigate its potential impact on users. In terms of information dissemination, it is also essential to examine not only the mechanisms through which threats spread but also the factors influencing user judgment. The overlapping area among these three themes is a new theme called “cognitive security,” which is security research that focuses on the impact on human cognition and decision-making through the interactions between attackers, users, and the information environment (Fig. 1). Traditionally, despite recommendations to use psychological methodologies and interdisciplinary approaches in research on technologies and theoretical frameworks to support appropriate decision-making and organizational-policy formulation that account for diverse user attributes, research focusing on psychological methods and cognition is currently significantly lacking. Therefore, focusing on cognition, I have established “cognitive security” as a theme to (i) counter “cognition-related threats” (Table 1), such as cyber fraud and social engineering, targeting individuals in the short term and (ii) false or misleading information and algorithmic manipulation aimed at manipulating cognition, decision-making, and people’s behavior in society and organizations.
Cognitive security can take three approaches: (i) how attack methods affect cognition (understanding cognitive abilities and cognitive processes); (ii) how interventions in cognition affect autonomous decision-making (countermeasures for cognitive abilities and cognitive processes); and (iii) how cognition and the effects of interventions change (or not) when people are in groups (understanding and countermeasures for collective cognition). In other words, it is an interdisciplinary theme that involves not only information science but also cognitive psychology and aims to solve the problem of methodologies and practices for protecting individuals, organizations, nations, and society from the effects of cognitive and information manipulation by maintaining autonomous decision-making in hostile situations. It is important to question and update your experience and knowledge rather than relying solely on them—What do you keep in mind as a researcher? Normally, one has many opportunities to advance research by using one’s experience and knowledge, and in some cases, one may unconsciously view these attributes as absolutes. However, I realized that my experience and knowledge can also be hurdles. From this realization, I have become conscious of the importance of questioning and updating my experience and knowledge instead of relying solely on them. My research often involves experiments involving people. Once, I wrote a paper on the results of an experiment that I conducted involving Japanese participants in Japan; however, on peer review, the paper was rejected; the reviewer pointed out, “Why conduct the experiment in Japan? Are the results of the experiment generalizable?” This experience led me to believe that to be accepted as a paper for international journals or conferences, it is only natural that the experiment should be conducted in Europe or the United States rather than Japan. I thus continued my research but shifted it to survey Westerners in English and summarize the results in papers, even though I was living in Japan. I began to feel frustrated and conflicted about the fact that despite my research being based in Japan, I was unable to directly address the actual situation in Japan. I also began to feel uncomfortable about the research trend of naturally targeting only Westerners. This uncomfortable state of mind was the trigger that led me to write the aforementioned paper on the theme of quantitative analysis of geographic skew in user-survey research in the fields of security and privacy [1]. Through this research, I showed that even in quantitative research, if there is skew in the environment or status of the subjects, it can pose a problem for the universality of the research field. This experience made me realize that it is important to sometimes question and update matters instead of solely relying on my experience and knowledge. Step outside your field of expertise with courage and curiosity to foster mutual understanding and shared motivation—Do you have a message for future researchers? Some social issues cannot be addressed by research in one’s field of expertise alone. Addressing these issues requires an interdisciplinary approach. To promote interdisciplinary research, it is important to have the courage to step outside one’s field of expertise. Even if you are an expert in a certain field, once you step outside that field, you become a novice, and that scenario can be scary. However, you can overcome this fear by being curious as a researcher. When you collaborate with experts in other fields, you can find common ground and understand each other. Conversely, by viewing the differences as interesting, you should be able to deepen your understanding. It is also important to share motivation. Even if your field of expertise differs from others, by sharing the same motivation, you can work together despite differences in experience and knowledge. Many of my research topics are interdisciplinary, and I have come to realize this fact through my experiences. Research fields have become increasingly specialized, and we get more opportunities to step into interdisciplinary areas concerning not only these societal issues but also everyday research. It is thus important to step outside your field of expertise and strive for mutual understanding and shared motivation. References
■Interviewee profileMitsuaki Akiyama received an M.E. and Ph.D. in engineering from Nara Institute of Science and Technology in 2007 and 2013. Since joining NTT in 2007, he has been engaged in research and development on cybersecurity. His research interests include cybersecurity measurement, offensive security, usable security and privacy, and cognitive security. |
|||||||||