|
|
|
|
|
|
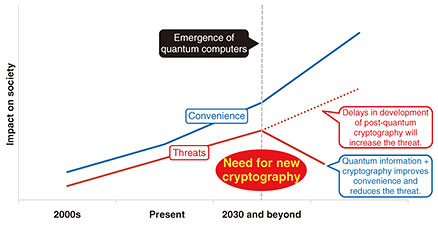
Rising Researchers Vol. 23, No. 10, pp. 14–19, Oct. 2025. https://doi.org/10.53829/ntr202510ri1  Next-generation “Secure Public-key Cryptography” as a Solution to the Rapidly Growing Digital ThreatAbstractTo prevent cyber-attacks, which are rampant on the Internet, encryption of data and communication content has become essential. Quantum computers—said to be 100-million times more powerful than conventional computers for specific tasks—are expected to be put into practical use in the 2030s. As quantum computers become more widespread, the digitalization of society will further progress, and the need for security technologies to support a digital society will also increase. In this interview, we spoke with Fuyuki Kitagawa, a distinguished researcher at NTT Social Informatics Laboratories and leader in research into next-generation public-key cryptography using quantum technology. Keywords: public-key cryptography, quantum cryptography, digital currency Technologies essential for security in the digital environment of the quantum-computing era—First, what kind of research is “secure public-key cryptography”? In today’s rapidly advancing digital society, digitized products and services are now indispensable. As semiconductor technology advances to support faster communication environments, such as fifth-generation mobile communications systems (5G) and 6G, and quantum computers emerge as predicted in the near future, it is highly likely that computing power will continue to increase significantly, and the digitalization of society is expected to progress even more rapidly. For example, the emergence of digital money, as exemplified by train-ticket payments and over-the-internet transactions, has greatly improved the convenience of everyday life. However, these digital currencies and digital transactions have also given rise to many fraudulent uses and crimes unique to the digital world. While the digitalization of society has dramatically improved convenience in many ways, it has also created risks that had not existed. Despite recognizing the convenience of using digital services, users who are more aware of these risks tend to be hesitant to use such services. Digital technology still faces many challenges, and security is an essential challenge to developing it so that it can be used more safely and securely by everyone. One of the most representative methods for protecting digital information is public-key cryptography. Under the expectation that quantum computers will become practical in the 2030s, research on public-key cryptography is currently undergoing a period of transformation. One reason for this transformation is that when quantum computers become a reality, situations will arise in which security cannot be ensured with conventional cryptographic methods. It has already been discovered that encryptions by using conventional public-key cryptographic methods, such as RSA (Rivest-Shamir-Adleman) encryption and elliptic-curve cryptography, can be easily decrypted with quantum computers. This discovery is shocking because RSA encryption and elliptic-curve cryptography are widely used for everything from our email correspondence to transactions by financial institutions. To prevent confusion even if research and development (R&D) on quantum computers is accelerated and quantum computers are suddenly put into practical use, R&D on public-key cryptography that produces encryptions that cannot be decrypted even by quantum computers is currently being pursued. The theme of this research is called “post-quantum cryptography.” As the implementation of quantum computers draws near, researchers are attempting to develop new cryptographic technologies that use the unique properties of quantum computers. As one such attempt, my research aims to use the incredible capabilities of quantum computers, which can even break encryptions by using “secure” encryption methods such as RSA, to develop cryptographic technologies that have hitherto been inconceivable. The theme of this research is sometimes called “quantum cryptography.” The ultimate goal of my research is to use my areas of expertise (cryptography and quantum information) to develop a quantum cryptographic method that will guarantee security—even in the future quantum-computer era—and ensure everyone can enjoy the benefits of a digital society (Fig. 1).
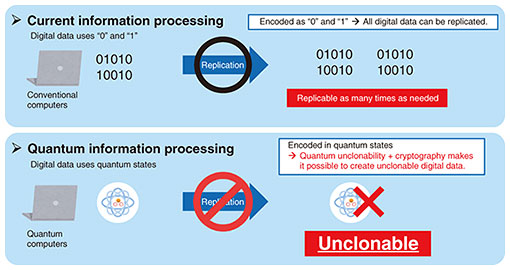
—Specifically, what kind of technological research are you conducting? Towards a secure digital society of the future, I aim to create “unclonable digital information”—even once quantum computers are put into practical use—by combining cryptography and quantum information. Regarding current information processing, all digital information is nothing more than a bit string consisting of a combination of 0s and 1s, and, theoretically, all digital information can be easily copied. We copy files on our personal computers and share photos with friends on social media on a daily basis. The ability to copy such digital information is convenient, but it also poses a risk to digital information. This convenience and risk of digital technology go hand in hand. Once all digital information falls into the hands of malicious users, it becomes a risk that it will be replicated without restriction and spread instantly. Cases of industrial espionage leading to the leakage of important trade secrets and theft of patented technology have been reported, and more familiar cases include the illegal downloading of books and music. A function for notifying the original owner of copies of digital information by other people is not currently available; consequently, the original owners only realize that their digital information or data has been copied and misused after it has been spread. In light of the risks mentioned above, processing using quantum information can eliminate the problems with current information processing and create digital information that cannot be replicated. It will also be possible to analyze information on cases of unauthorized duplication and misuse. With this processing method, digital information is encoded using “quantum states (or qubits)” that represent the state of each quantum bit. Quantum states are unclonable, so it is impossible to devise a technology that can clone any quantum state perfectly. Combining quantum information processing, which involves an extremely large number of states, with cryptography will make it possible to create “unclonable digital information”—namely, information that is cryptographically secure in terms of not only complete cloning but even partial cloning being impossible (Fig. 2).
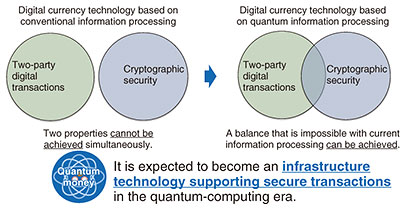
To create this unclonable digital information, I’m conducting research that combines quantum information processing with cryptography. I’m currently focusing on research on unclonable digital currency (quantum money) as an application of quantum information processing (Fig. 3). To date, I’ve proposed methods and related technologies for this digital currency and presented my research findings at major international conferences on cryptography and quantum information, where they have been appraised favorably.
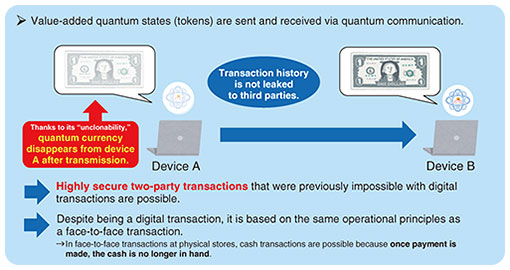
—What challenges have you faced during your research and what challenges do you anticipate in your future research? One challenge is that it is not possible to demonstrate the methods and technologies we are developing because an actual quantum computer does not yet exist. We are currently designing methods under the assumption that an ideal quantum computer will be created, and our goal is to complete algorithms before the hardware is developed. Although we have made considerable progress in this direction, the next step is to monitor the development status of quantum-computer hardware and improve and refine our methods so that they can be implemented in a realistic environment. Completing the theory in advance should also provide guidance and have a positive impact on development of hardware. Positioned at the boundary between cryptography and quantum information, my research field is sometimes called “quantum cryptography.” Research in this field is progressing rapidly as the implementation of quantum computers becomes closer. A huge number of results have been produced and published one after another at a dizzying pace. There were many times when my group’s research results competed with those of other groups. The number of papers submitted to CRYPTO, the international conference on cryptography, increased from around 500 in 2024 to 650 in 2025. This figure is not the total number of submissions to all conferences on cryptography, and the increased number of submissions cannot be solely attributed to advances in quantum cryptography; even so, this example makes it clear that research in this field is progressing rapidly. I think it is easy to understand our concern that if we’re not careful, other groups might preemptively announce what we’re working on. Unless research is carried out in a planned and swift manner, it will be difficult to take the lead in this field, so we must be mindful of that point. Secure quantum money will transform buying and selling into fully two-party transactions—What are your prospects for future research? My current goal is to use quantum information to enable “fully two-party transactions.” The unclonable digital currency that I’m currently researching is known in the research community as “quantum money” and this revolutionary technology is expected to change the concept of digital currency. The most impressive feature of quantum money is that it will enable two-party digital transactions with extremely high security in a manner that would not be possible with conventional information processing. With conventional digital currency technology based on cryptography, transaction monitoring by a third party is an essential function to design into a secure system. Currently, the only way to ensure cryptographic security is to designate a decision-making authority (such as a bank) as the third party, get them to communicate the details of the transaction to the receiver, and have them transfer the funds from the account of the sender to that of the receiver. This method, however, leaves the possibility that all transaction histories can be collected by the third party (the decision-making authority). Knowing this possibility, potential users of digital currency feel uneasy and reluctant about using it, and those feelings could be an obstacle to the widespread adoption of digital currency. In contrast, as mentioned above, unclonable quantum money enables cryptographically secure, fully two-party transactions. Regarding quantum money, quantum states are assigned value, and users can make payments by sending and receiving these quantum states in the same manner as cash. It is not necessary for a third-party decision maker to be involved in the transaction. This type of cryptographically secure, fully two-party digital transaction is possible only because of quantum information processing, which, unlike conventional information processing, makes it impossible to replicate digital information. Using quantum money enables the act of sending currency and receiving goods securely online anywhere in the world, just as if the two parties were buying and selling face-to-face in a physical store (Fig. 4). The deployment of this technology throughout society will obviously require separate legal and political responses.
While I’ve used the example of unclonable digital currency in this interview, I’m also simultaneously researching other applications of quantum information, such as “unclonable software” and “unclonable encryption keys.” I believe that since the effective use of quantum information can lead to new applications and research, its possibilities are endless. —Would you tell us about relationship between your current research and NTT business? Digital transformation is one of the pillars of NTT’s business. Building a robust platform that supports the expansion of a digital society is a key challenge for NTT. Combining user ideals (fully two-party transactions) with high security (cryptographically rigorous security guarantees), quantum money is an appealing technology for supporting digital infrastructure in the quantum-computing era. With that challenge in mind, I hope to implement the secure quantum money that I am researching, thus contribute to the construction of a solid digital platform. As the implementation of quantum computers draws near, quantum computing and quantum cryptography are research areas attracting global attention. My research is not about developing quantum computers; rather, it is about addressing the anticipated conveniences and risks that may arise from them. However, I believe that producing innovative research results in these research areas is effective in showcasing NTT’s technological capabilities to the world and important from the perspective of strengthening the competitiveness of our global business. With those facts in mind, I’m working day in and day out on producing such innovative research results. —What led you to join NTT? I joined NTT as a researcher in 2019. The main reason I wanted to join the company was my internship at NTT laboratories during my first year of doctoral studies. Even back then, NTT laboratories were home to many world-renowned researchers in the field of cryptography, and while most internships last around one month, my internship lasted two months. Those two months were extremely stimulating. Through experiencing a positive outcome of that internship, I was able to present my research at an international conference called “EUROCRYPT,” where it was highly praised. During the internship, a world-renowned researcher at NTT approached me and asked me if I wanted to work on long-term research together, and that offer was a major factor in my decision to join NTT. Thanks to that experience, even after returning to university, I naturally began to think it would be great to work at NTT laboratories. Therefore, after completing my doctoral program, I applied to NTT laboratories as my desired career path and, fortunately, was accepted and joined the company. Looking back now, I feel that having my aspirations fulfilled during my internship was perhaps my destiny. —What is your impression of your current workplace, NTT Social Informatics Laboratories? NTT Social Informatics Laboratories conducts R&D of technologies that contribute to the transformation and development of social systems and human society, which are becoming increasingly sophisticated through information and communications technology. A key feature of our research is that we focus not only on R&D of technologies that will be useful immediately but also on steady basic research aimed at creating technologies that will enrich social life with a long-term perspective. We conduct a lot of R&D—and my research is one such example—with an eye toward social developments 15 to 20 years from now. Although NTT Social Informatics Laboratories is a corporate research institute, one of our major characteristics is unwavering commitment to conducting truly valuable research without being fixated on short-term profits. NTT Social Informatics Laboratories conducts research in several fields, one of which is security and cryptography. Cryptography research at NTT has a long history and is highly regarded both domestically and internationally. This status is evidenced by the fact that each year, outstanding professors, researchers, and interns from around the world visit our Cryptography Research Group. As a researcher, I find it extremely rewarding to be able to work on cutting-edge research and discuss it with such researchers from around the world. I feel that—unlike any other in Japan—our Laboratories offers a unique environment for cryptography research. —Would you give us a message for researchers, students, and business partners? A theory I’ve had since I was a student is that the best part of research is discussion. I enjoy the time I spend silently solving problems on my own, but the process of sharing and discussing my thoughts with various people and producing good results is truly enjoyable. Whether the person I’m talking to is a researcher or a student, I can sometimes learn something from them, even if they haven’t studied basic theory. For example, when I explain technical terms, I can discover a problem from the questions they ask, realizing, “Oh, so that’s the part they don’t understand,” and this realization can serve as reference the next time I give lectures to people in the same situation. Sometimes casual conversation can lead to good outcomes, and I have experienced and felt the power of debate and discussion many times. I hope to continue such discussions and move forward together towards a better future. Finally, I’d like to say a few words to all students. As a research institute that recognizes the importance of basic research, NTT laboratories believe that steady accumulation of basic research leads to the creation of truly innovative technology. For students who share this belief, I wholeheartedly recommend NTT laboratories as a research environment, and I look forward to the day that we can engage in extensive discussions and conduct research together.
■Interviewee profileFuyuki Kitagawa completed his Ph.D. in cryptography at the School of Computing, Tokyo Institute of Technology in 2019. He joined NTT in the same year. In 2024, he became a distinguished researcher at NTT Social Informatics Laboratories. He has been engaged in research in the interdisciplinary field of cryptography and quantum information. He received the Institute of Electronics, Information and Communication Engineers (IEICE) Technical Committee on Information Security (SCIS) Best Paper Award in 2015, the Tokyo Institute of Technology Teshima Seiichi Memorial Research Award (Doctoral Thesis Award) in 2020, and the IEICE SCIS Innovation Paper Award in 2025. |
|